How I Defeated the NSA!
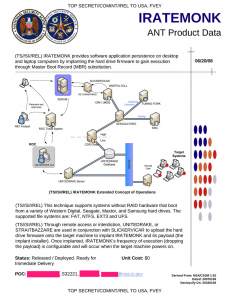
IRATEMONK page from the NSA ANT catalog
Well, maybe “defeat” is too strong of a word, because as Gollum says of the Nazgul, “you cannot defeat them!” BUT, I have ample evidence that measures I put into place years ago made one of my companies products highly resistant to an attack by the NSA. I’ll explain below.
As many of you know, I work as a cyber security researcher and architect. I currently work at a large computer hardware company that I won’t name here, but it’s pretty easy to figure out which one. Back in 2009, I was working on solid state drive (SSD) data security. SSDs are used for local storage, performing the same function as a hard disk drive but using memory chips rather than a magnetic disk to store the data.
Back then, computer security was seen more as a necessary evil rather than an essential primary function of a computer. In other words, the general thought was that you only implement security features if absolutely necessary, it cost money and didn’t generate a visible return on investment. That meant I had the difficult job of trying to convince the “higher ups” that we really need to add security to our products.
I lobbied extensively for a particular security feature called “firmware signing.” This is a technique that uses cryptography to make it difficult to make unauthorized changes to the device firmware. Given that the firmware controls every aspect of a device, this seemed to be essential. Back in 2009, most if not all hard disk drives and SSDs did not use signing. This is a very bad thing!
Consider that if just anyone could update your firmware, they could simply wipe it out or erase all your data. Or they could plant some malicious code to spy on you. This could happen surreptitiously over the internet while you visit a website, for example.
Anyway, I was able to convince, cajole and outright usurp my management at the time to put this security in place. I was successful, but viewed more as a pain-in-the-ass rather than a “savior,” simply because there was no short-term payback.
Fast forward to today. Malware and spyware is everywhere, it is a multi-billion dollar industry worldwide and involves everyone from mischievous teens to highly organized criminal enterprises to nation-states. The security posture of our computer network is pathetic, but getting better.
In May, I saw a report that mentioned The Equation Group and how they exploit firmware. The name “Equation Group” is made up by security researchers who found and classified the malware. To quote the report,
“The ‘Equation Group,’ named for its affinity for ultrasophisticated encryption schemes and associated malware, is now among the most sophisticated threats ever observed.”
Thus, because of it’s sophistication, it is associated with a nation-state attacker, meaning the government of a country. Other evidence, such as the page from the leaked NSA ANT catalog, an internal NSA catalog of spy instruments and software, indicates that this is probably the work of the National Security Agency. The particular product that attacks hard drive or SSD firmware is the IRATEMONK, shown at the top of this post.
So… What evidence do I have that I defeated the NSA? The list of drives known to have been infected by The Equation Group (probably NSA) come from companies such as Seagate, Maxtor, Western Digital, Samsung, IBM, Micron and Toshiba. My company is NOT on that list, and it is likely because of the firmware signing I pushed through way back 2009 when almost no one thought this possible.
Given the secretive nature of this business, that is probably as good of evidence you can get to prove you did your job well!
Posted in Cyber Security by Mark with comments disabled.