Coolest Patent Ever Granted
Sensor Privacy Mode, Granted the Day After the Eclipse
Today the United States Patent Office granted one of the coolest patents ever: Sensor Privacy Mode, on which I am the first inventor. It is a relatively simple yet powerful technique to put the control of privacy back into the hands of the users. Basically, it prevents your own phone, computer, mobile device or anything with a sensor from spying on you on behalf of someone else. And it does this in a way that is undetectable to the party attempting to spy.
Link to patent is here.
Do you know how to determine if a patent is of high value? One way is that you find there is a huge high-level corporate fight by people trying to get named on the patent as an inventor because the idea is so powerful. Yes, that happened with this patent.
Posted in Cyber Security by Mark with comments disabled.
Sharing “Cyber Secrets” with Russia?
Is There A Problem with This?
Yesterday Reuters had a headline article about how western tech firms share cyber secrets with Russia in order to sell their products in Russia. You can read the article here.
In my opinion: This is a sensationalized story written to fit in with the times. Here’s why:
- Western tech firms are not intentionally “sharing” cyber secrets.
- Tech companies will do essentially anything it takes to gain entry into a lucrative market. Always have, always will.
- Security functionality should only depend on a small set of secrets, such as a key that cannot be examined by anyone. Encryption algorithms, authentication techniques and security functions should not rely on being secret and as a matter of fact, if they are it is viewed as a bad implementation.
The Reuters story focuses on the current boogeyman country Russia, and mentions China. The Chinese government has an arguably tighter grip on the Chinese economy, is far more paranoid than Russia and is at least as aggressive in cyber spying. The Chinese market is so large that western companies will bend over backward to get into it. Here is an example:
All PCs have a little crypto processor called a Trusted Platform Module, or TPM. If you’ve ever used Microsoft Bitlocker, you’ve used the TPM on your machine. The TPM implements security algorithms developed by open standards committees, everyone knows what goes on in a TPM (or could know if they wanted).
China doesn’t like the TPM because they either don’t trust westerners to develop secure algorithms, and probably because the TPM has no backdoors, or ways for the government to get around the encryption. More specifically, the Chinese don’t like the security algorithms in the TPM.
Ok, now a PC maker doesn’t want to make a special motherboard for China only, or change their software to operate differently in China. You know what the solution was?
China devised their own TPM algorithms and had western PC makers put those algorithms in the Chinese market TPM instead of the open standards algorithms. The suspicion in the security community is that these algorithms have backdoors that only the Chinese government is aware of.
Western PC manufacturers will happily follow the Chinese government rules and implant spy devices on PCs meant for China. Most companies would be staunchly opposed to this suggestion from the U.S. government, arguing that they don’t exist to manufacture spy devices for the government. Yet that is what happens in China.
What is going on in Russia is nothing new, except apparently importing to Russia becoming more strict. You really can’t blame the Russians (or anyone else) for worrying about backdoors in western-built products, the stories about the NSA implanting secret access have been all over the internet. Companies are usually open to having a “trusted third party” examine their code and products to ensure no backdoors are present. This is not “sharing secrets” as the third party is severely limited in what they can disclose.
The Reuters article pointed out that Symantec ceased allowing code inspections because they did not trust the trusted third party, probably for good reason. The fear is that the third party was actually looking for security vulnerabilities as an agent for the Russian government. Indeed, if the third party is not trusted, the procedure does not work.
BUT, the interest of western companies is heavily weighted to protecting intellectual property rather than worrying about vulnerabilities in code. That is more likely the reason Symantec dropped out of the program. They are, after all, in the software security industry and if their code was broken well then their business is ruined. So in their case, hidden vulnerabilities are, in a sense, intellectual property to be protected.
Personally, I’d be happier if the U.S. government required such code inspection on imported products. We know spyware is implanted in Chinese-made items. This would simply become consumer protection, hey you can spy on your customers but at least disclose it. I doubt it’s practical, though, given the vast number of imported products to the U.S. and the dearth of interest in the government to seriously protect cyber infrastructure.
Posted in Cyber Security by Mark with comments disabled.
Need for Federal Laws Regarding Handling of Personal Data
Are you worried about government agencies spying on you?
Well, that isn’t the only problem you should be concerned about in this area:
“Detailed information on nearly every U.S. voter — including in some cases their ethnicity, religion and views on political issues — was left exposed online for two weeks by a political consultancy which works for the Republican National Committee and other GOP clients.”
Less than a century ago, this kind of information could land someone in a concentration camp, thus the EU has fairly strong data privacy laws today. Not so in the U.S.
It can be done. Laws have been made in the past, such as HIPAA laws that protect medical data. Unfortunately, the most powerful corporations in the world are dead set against such laws so there is a huge barrier to overcome.
Posted in Cyber Security by Mark with comments disabled.
Dark Foreboding of “WannaCry” Malware (Part 2)
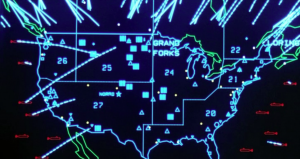
Incoming! Ahhhhh! (From the movie WarGames)
The pic above is the display at NORAD of incoming ICBMs as dramatized in the best hacker movie ever made: WarGames. The underlying theme was that a high school student hacks into a government supercomputer and nearly starts a nuclear war by accident. I love this movie, the hacker is using old pre-IBM and pre-Apple microcomputers and a phone modem to explore and hack the digital telecom of old: the landline phone system. He also used his skills in non-computer ways to keep one step ahead of his government pursuers, like opening an electronic lock by tape recording the keypad tones and playing them back, and by hacking a pay-phone system by reproducing clicks to bypass the pay box. Just about everything he does (sans the beautiful girlfriend of course) is classic hacker. And this was 1983!
An interesting piece of trivia: President Reagan saw this movie and asked his staff if it could happen in reality. They investigated and reported back that it was far worse than portrayed (!) which led to the first cyber-security National Security directive to be issued by a president.
The WannaCry event should be a wakeup call (really one of many) to the government. At a minimum, some sort of agency should become responsible for cyber security infrastructure defense. I also believe the USG should enact laws that require at least a minimum amount of security be built into all computing devices sold in the country. We do it for radio emissions (the FCC label you see on all computers) and power safety. For healthcare it’s the FDA certs, for airplanes it is the FAA. The FAA is now regulating toy drones, seems like cyber security could be regulated at least a bit. Having been in the computer industry for decades I can say it will hardly make a dent in manufacturers profit, even though they are certain to complain of any new regulation in this area. Example: Some of the best smartphone security exists in iPhones. Apple is wildly profitable.
The Shadow Brokers are now saying in their fake broken-english writing that they will release more leaked code like a “…wine of month club[SIC].” They also claim to have nuclear program secrets that makes the WarGames reference above apropos. So we are looking at possibly larger hacking attacks and maybe even a nuclear hacking attack. Oh boy. And we haven’t seen the worst of the Internet of Things problems yet…
Stay tuned…. If you can!
Posted in Cyber Security by Mark with comments disabled.
Dark Foreboding of “WannaCry” Malware (Part 1)
This Can Be Made into a Powerful Little Cyberweapon
The WCry malware, also called “WannaCry,” has made headlines since last Friday for causing computer problems around the world. It is now probably the most infamous virus ever due to the breadth of its effect, and effectiveness. There is a multitude of malware “in the wild” that behaves in a similar fashion, so why is WCry so bad?
WCry operates by invading computers through vulnerabilities in certain operating systems, primarily Microsoft WindowsXP and later versions of Windows that have not been updated with patches (small fixes to the operating system software). Attacking a computer in this manner is nothing new, it happens quite often.
What is bad now: This vulnerability is newly revealed (a zero-day), it is in many older systems (millions), and step-by-step instructions on how to exploit this zero-day were released by the Shadow Brokers. Modern systems are not affected by this virus but there are many older systems out there not properly managed, including in critical infrastructure as the hospital in Great Britain and the Russian government.
WCry is ransomware, encrypts your data and demands ransom to be paid in Bitcoin currency to decrypt your computer. Bitcoins are nearly impossible to trace and therefore used famously for money laundering. Ransomware is again not new but…
What is bad now: The use of ransomware is growing and the scale of this attack is an unprecedented use of ransomware. Ransomware is bad, if your drive gets encrypted it’s all over. Even if you pay the ransom, there is no guarantee the drive will get encrypted. So far the U.S. government has said no one who has paid the ransom has gotten their data decrypted.
WCry was developed by cyber criminals and possibly North Korea. It was not developed by the NSA. The NSA used the vulnerability for years (not as ransomware but presumably to spy) and never told Microsoft, so it could not be fixed. Now it turns out that the NSA apparently secretly told Microsoft about it after the NSA discovered that it had “leaked” to the Shadow Brokers. Microsoft raced to fix the bugs just weeks prior to the Shadow Brokers releasing the exploit to the public.
Why this is bad now: It originated from our own government. We know the NSA, CIA, FBI, and you-name-it-three-letter-got-agency “hoard” these vulnerabilities, probably independent of each other. Where is the government agency responsible for protecting the United States from attacks on these vulnerabilities? An independent cybersecurity researcher in Great Britain discovered a way to temporarily stop WCry. Why isn’t there a government agency at least trying to do protect our cyber systems in real-time? We have an enormous agency looking for and preventing terrorism, what about cyber crime?
Why this is really bad! It’s not over, already two other exploits have been discovered using the same NSA-leaked exploit.
By the way, the pic at the top of the post is my latest project: It is a low-cost single-board computer with a powerful processor and operating system used by hobbyists. It includes built-in wifi and bluetooth radios. It is the size of a credit card. More devices than you can imagine can be connected to this hardware, think cameras, microphones, location detectors, etc. You might imagine that it could be used in nearly unlimited “less than honorable” ways.
Posted in Cyber Security by Mark with comments disabled.
Superyacht Cybersecurity Consultant Available
Vulnerable to Cyber Dangers?
Sirs:
I bring to your attention this article on “super yacht” cyber security, and in fact, the severe lack thereof: Click here for the link. Make no mistake, this is a fundamental safety and privacy issue that I have personally verified.
Given that I am a uniquely qualified expert in cybersecurity and marine cyber systems and electronics (perhaps one of the very few in the world), I solicit my services to owners, operators, and representatives of such vessels. I offer expert evaluation and recommendation of not only secure systems but also privacy. I guarantee the utmost discretion and privacy for all my clientele.
My linkedin resume is available here: Mark’s Linkedin resume.
Email contact at m.scottnash@comcast.net
Thank you for your consideration,
Mark Scott-Nash
Posted in Cyber Security, Sailing by Mark with comments disabled.
Real, and Disturbing News
Cyber Intelligence is NOT Limited to These Two Agencies
While you were being distracted by inane presidential posts and accusations of fake news, real news was being made in the government intelligence organizations. Since last September there have been two major releases of secret cyber weapons leaks. The National Security Agencies tools were released by a mysterious group calling themselves “The Shadow Brokers,” which I initially wrote about here. Then, several weeks ago Wikileaks published tools lost by the Central Intelligence Agency which I wrote about here.
So the two leading cyber spying agencies of the most powerful nation in the world had many of their cyber weapons exposed in less than a year. If that isn’t deeply concerning to you as an American citizen or even more broadly, as a citizen of the “Five Eyes” intelligence-cooperative countries, then you should more closely examine what the mission of these agencies are: They are not here to spy on citizens, they exist to keep the United States safe and further the interests of the country you live in.
The CIA and NSA leaks are not the only rumblings currently rocking nation-state intelligence organizations. This article describes some of the back-and-forth of a cyber cold war. It enumerates many recent events surrounding these leaks and other activity such as arrests and “official” revelations of the cyber-spying ability of the US. The article contains lots of speculation and guessing about what is secretively going on between the US an possibly Russia. Make no mistake, this is definitely an attack on the US. Have you seen any Russian cyber weapons leaks? Chinese? Israeli? Nope.
I find this stuff fascinating, especially the fact that with the vast access to public information today, you can piece together a lot of very different sources and come up with a highly plausible scenarios of this secretive cyber war.
I have to agree with the author that there is something big going on and the public won’t know for sure for a long time how the hacking tools were leaked or who specifically is “attacking” the US by releasing these tools. That Russia is behind the leaks is a good guess, however I disagree with the author that Russia is the only country that has both the ability and motivation to attack the US like this.
As I have stated in the past, building cyber weapons is not that difficult in comparison to physical weapons like nuclear bombs. To get away with building a nuke today, you need an army of PhD scientists and engineers, significant industrial capacity and need to expend extreme effort to keep the program under wraps. All a cyber weapon program requires is a few hackers, computers and the internet. No PhD required, many of the best hackers in the world had not graduated high school.
So, North Korea has built nuclear weapons. Do you think they can build cyber weapons? And why limit our guesses to our most notorious enemies, really any nation can do this.
Oh, and so can many big corporations, which have exactly the same talent, have the money and are producing a myriad of spy devices that you carry around in your pocket every day.
Posted in Cyber Security by Mark with comments disabled.
The Secret CIA Files, Part 2
I thought I was done writing about this incident, but in fact no. This morning I listened to the BBC Global News podcast, as I do most days, and heard a story about this breach. The story explored several angles of the Wikileaks CIA documents but one was of particular note: An interview with an ex-CIA agent and his analysis of the impact “if” these were authentic. It was completely off target. Here’s why:
First he essentially insults “engineers” as being “odd” and building cool products without regard to security. This is patently false. Engineers build to products to specifications decided on by executives and managers. This includes product features, what will and will not be fixed, and most decidedly, security. The overriding motivation behind each decision is to maximize profit (time to market, cost of development, what the competition is doing, you name it). Security invariably falls to the bottom of the list of where to put resources. Security problems are not due to engineering shortcomings.
I have to emphasize this, engineers are NOT to blame for the security holes in released products. Period.
I don’t expect a CIA agent to know this, of course. But then he went off track again and parroted what a lot of the media is thinking, which is incorrect. And to be honest, it makes me wonder if this guy WAS an ex-CIA agent.
This agent went on to describe the damage done by this release as enabling attackers around the world to “come after us” by using the CIA tools and techniques. This is patently false. Why?
The CIA does not have a monopoly on cyber spying tools, nor will they ever have one. All the vulnerabilities that the CIA documents describe could have been found by anyone, and indeed were. One of the leaked documents describes how the CIA acquired knowledge of vulnerabilities, and this included BUYING them from cyber security researchers who found them. Really? So Russia, North Korea and Iran couldn’t buy them as well?
Building cyber weapons is not in the same class as building a nuclear bomb, for instance. Unfortunately, cyber weapons could potentially be far more effective than nukes, especially against the internet-dependent United States. To build a nuclear weapon, you need refined plutonium or uranium. This is extremely difficult to do and the world is watching for it. Building a cyber weapon requires money. That’s all, money. A group of individuals could have the same “cyber-power” as any nation-state in the world if they simply had the money to invest.
The real problem with the CIA leak is not that the “enemies” have new cyber spy tools, but that the CIA now has to start from scratch and build new ones. That is the angle the media is missing. All the vulnerabilities described in the documents have apparently been fixed, possibly because the CIA knew about the breach months ago and warned the companies whose products were affected. If so, kudos for the CIA for, in the end, doing the right thing.
All nation-states are cyber-spying, as well as many other actors (corporations, criminals, hacking groups, and organizations that you never hear about). These documents do not reveal anything new to them. However, the CIA cannot now use all the tools they developed at great expense and they will have to write new ones.
I’m not worried that the CIA is spying on Americans, as many media outlets imply. It is illegal for them to do so, but if that doesn’t ameliorate your concern, they could have spied on you before the computer age too. No need to be more concerned now, in my opinion. They are spying, that is their job. I don’t see how the U.S. can survive without such agencies. But like the NSA, they ironically don’t seem to have much control of their own internal security.
Posted in Cyber Security, Sailing by Mark with comments disabled.
The Secret CIA Files
It’s been windy for several days now, too windy to sail anywhere and almost too windy to even get off the boat. Shelly has been taking advantage of this time to work on her new iPhone app. I had run out of projects to do and was getting fairly bored. Until today.
Why did I tag this under the “sailing” category? Because if we were sailing, I would not have investigated this to the degree that I did. Ignore the rest if you are not interested in cyber security.
Yesterday, Wikileaks published the first part of semi-raw data supposedly leaked or stolen from the Central Intelligence Agency. The documents supposedly cover the CIA’s cyber spying operation and Wikileaks claim it is “…the largest ever publication of confidential documents on the agency.” Wikileaks claims that the CIA employs at least 5000 “hackers,” as Wikileaks characterizes them, and characterizes this as the CIA’s “own NSA.” This seems highly plausible as government agencies like to be completely independent of each other even though there is a lot of overlap. Overlap with the NSA in this case, or really any number of other three-letter agencies who employ “hackers” such as the FBI, DHS, etc.
Having somewhat of a professional interest in this area (and nothing better to do), I sampled some of what Wikileaks released. Specifically, I looked at a cryptographic requirements document and a “tradecraft” document.
The crypto requirements for their software spy tools is excellent and the tradecraft doc, which describes special practices necessary when writing spyware, enumerates robust techniques that a professional spyware creator would certainly use. Also, some of the trivial files, which appear to be from the personal directories of real people, look to me to be the kind of thing a professional “hacker” would have in their directory, whether in the CIA or not.
Many media outlets preface their stories about this with, “…if this is real.” In my opinion, based on a long career working with, and against, the type of people who would create such spyware, as well as my specific experience in the cyber security realm, this is either an extremely well done hoax or it is the real deal. If this were a hoax, I can’t imagine any one or group who were not highly experienced in computer science, engineering, cyber security AND spyware techniques could produce such an archive and what would be the point if they did?
Media: This leak is real.
So unfortunately, this is yet another highly damaging leak in the United States cyber intelligence machinery. It is more damaging than the recent NSA leaks because these documents describe tools and techniques up to 2016, whereas the NSA leaks were not newer than 2013, if I recall correctly.
This will force the cyber intelligence agencies to rewrite a significant number of their cyber spyware tools, a very expensive proposition, though quite do-able. The good that comes from this? Apple, Microsoft, Google and many other cyber manufacturers will fix gaping holes in their products. Too bad the U.S. Government doesn’t have such an enthusiastic division dedicated to finding and fixing these holes, instead of exploiting them.
Expect things to get worse before they get better in the Internet-of-Things world.
Posted in Cyber Security, Sailing by Mark with comments disabled.
Government Surveillance Demands
Yes, It Can Be Hacked!
For cyber security types, here is a good article providing evidence that the FBI’s arguments for coercing Apple to break into the San Bernardino terrorists iPhone 5c were essentially propaganda. The FBI appeared to use this case to lobby for federal legislation to require “backdoors” to be built into smartphones, etc., so that law enforcement can gain easy access to any device.
The story went like this: The FBI wanted access to one of the San Bernardino shooters iPhones so they could check up on contacts, emails, text messages, anything that would help the FBI discover a potential (but as yet unproven) network or other terrorist contacts. The iPhone in question was locked with a passcode and if you make too many wrong entries trying to guess the code, the iPhone will erase all it’s memory.
The FBI decided to ask Apple to unlock it. Apple said that the FBI mishandled the phone and prevented the phone from uploading its memory to the Apple cloud. Apple said it did not have a way to unlock the phone itself and this is very likely true. The FBI then asked Apple to use their intimate knowledge of the workings of the iPhone to figure out a way to unlock the phone, basically to hack into their own product. Apple refused. The FBI then went public and in a very high profile case, attempted to use legal means to force Apple to comply.
After a couple of weeks of very public bantering, the FBI claimed it found a way to hack into the phone and asked that the case to force Apple to break into it’s own product be dropped. Subsequently, the FBI made several well-publicized pleas to congress to come up with a law that would force companies to build in “backdoors” to their products so the FBI and other law enforcement would not have to resort to expensive hacking techniques or even necessarily get a warrant.
The argument they make is that it would be a valuable tool to prevent terrorism and crime. And maybe it would. But the complexities of this issue go far beyond the myopic FBI viewpoint. Here is why:
A backdoor is a cyber security term for a method to bypass a user’s security. You have your key to unlock your “front door,” and the FBI has a key (or method) to unlock a built-in “back door.” This would work if the FBI kept their key safe. But suppose they did not keep it safe? Suppose a future highly placed individual in the FBI decided to use these backdoor keys to gather compromising information about political figures in order to gain power. What would J. Edgar Hoover have done with such power? Or Vladimir Putin?
Apple was correct to deny the FBI their services. No one buys an Apple (or any other brand) product with an expectation that the manufacturer is going to hack it open on demand. Privacy is expected and the product should operate as intended. Also, engineers would have had to produce a new technique under coercion of the law. The FBI could likely then use this tool to break into any other iPhone as it desired (and the FBI confirmed they have many iPhones they want to open up). Can the government force a locksmith to create a two-key lock if the locksmith does not want to? Is that constitutional?
Ironically, when the news of this broke, techies on the internet were abuzz with an easy technique to break into the iPhone: Take it’s flash memory out, read it and “brute force” guess the password (try every one until you find it). This would prevent the memory from being erased. And this is exactly what the proof-of-concept paper referenced in the above hyperlink explains.
The FBI thought this technique was “impossible.” Apparently, engineers and hackers are now the power brokers in this country. 😉
Posted in Cyber Security, Hacking! by Mark with comments disabled.